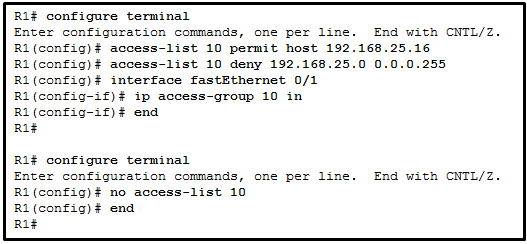
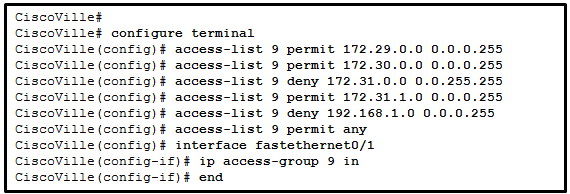
1. What does the CLI prompt change to after entering the command ip access-list standard aaa from global configuration mode?
access-list 100 permit ip host 192.168.10.1 any
access-list 100 deny icmp 192.168.10.0 0.0.0.255 any echo
access-list 100 permit ip any any
Which two actions are taken if the access list is placed inbound on a router Gigabit Ethernet port that has the IP address 192.168.10.254 assigned? (Choose two.)
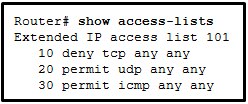
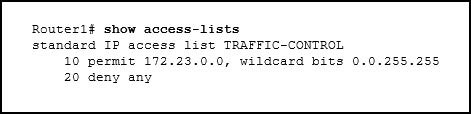
Refer to the exhibit. An administrator first configured an extended ACL as shown by the output of the show access-lists command. The administrator then edited this access-list by issuing the commands below.
- Router(config-line)#
- Router(config-std-nacl)#
- Router(config)#
- Router(config-router)#
- Router(config-if)#
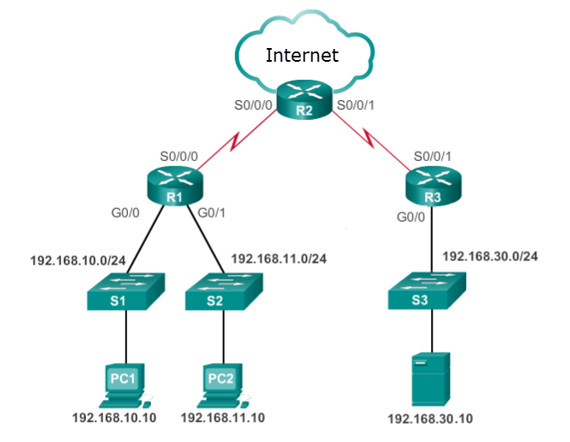
- extended ACL outbound on R2 WAN interface towards the internet
- standard ACL outbound on R2 WAN interface towards the internet
- standard ACL outbound on R2 S0/0/0
- extended ACLs inbound on R1 G0/0 and G0/1
- to remove all ACLs from the router
- to create an entry in a numbered ACL
- to apply an ACL to all router interfaces
- to secure administrative access to the router
- worm
- virus
- Trojan horse
- botnet
- financial gain
- fame seeking
- status among peers
- political reasons
- hacktivist
- cybercriminal
- script kiddie
- vulnerability broker
- a query and response protocol that identifies information about a domain, including the addresses that are assigned to that domain.
- a scanning technique that examines a range of TCP or UDP port numbers on a host to detect listening services.
- a software application that enables the capture of all network packets that are sent across a LAN.
- a network scanning technique that indicates the live hosts in a range of IP addresses.
- address spoofing
- MITM
- session hijacking
- DoS
- nonrepudiation
- authentication
- integrity
- confidentiality
- a digital certificate
- a different public key
- a private key
- DH

- access-list 1 permit 192.168.10.0 0.0.0.127
- access-list 2 permit host 192.168.10.9
access-list 2 permit host 192.168.10.69 - access-list 5 permit 192.168.10.0 0.0.0.63
access-list 5 permit 192.168.10.64 0.0.0.63 - access-list 3 permit 192.168.10.128 0.0.0.63
- access-list 4 permit 192.168.10.0 0.0.0.255
- destination UDP port number
- computer type
- destination MAC address
- ICMP message type
- source TCP hello address
- numbered standard
- named standard
- extended
- flexible
- Use the no keyword and the sequence number of the ACE to be removed.
- Copy the ACL into a text editor, remove the ACE, then copy the ACL back into the router.
- Create a new ACL with a different number and apply the new ACL to the router interface.
- Use the no access-list command to remove the entire ACL, then recreate it without the ACE.

- ACL 10 is removed from both the running configuration and the interface Fa0/1.
- ACL 10 is removed from the running configuration.
- ACL 10 is disabled on Fa0/1.
- ACL 10 will be disabled and removed after R1 restarts.

- The established keyword is not specified.
- The sequence of the ACEs is incorrect.
- The port number for the traffic has not been identified with the eq keyword.
- The permit statement specifies an incorrect wildcard mask.
- Router1(config)# access-list 10 permit 192.168.15.23 0.0.0.0
- Router1(config)# access-list 10 permit 192.168.15.23 0.0.0.255
- Router1(config)# access-list 10 permit 192.168.15.23 255.255.255.255
- Router1(config)# access-list 10 permit host 192.168.15.23
- Router1(config)# access-list 10 permit 192.168.15.23 255.255.255.0

- access-list 1 permit 192.168.10.128 0.0.0.63
- access-list 1 permit 192.168.10.0 0.0.0.255
- access-list 1 permit 192.168.10.96 0.0.0.31
- access-list 1 permit 192.168.10.0 0.0.0.63
- Router(config)# access-list 95 deny 172.16.0.0 255.255.0.0
- Router(config)# access-list 95 permit any
- Router(config)# access-list 95 host 172.16.0.0
- Router(config)# access-list 95 deny 172.16.0.0 0.0.255.255
- Router(config)# access-list 95 172.16.0.0 255.255.255.255
- Router(config)# access-list 95 deny any

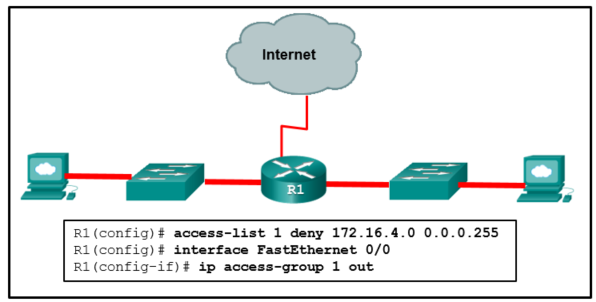
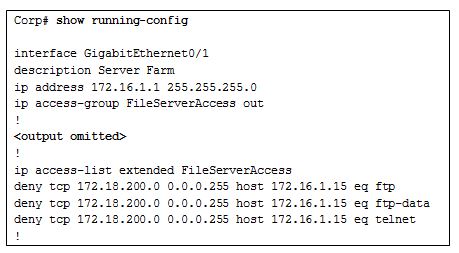
- The ACL should be applied outbound on all interfaces of R1.
- The ACL should be applied to the FastEthernet 0/0 interface of R1 inbound to accomplish the requirements.
- All traffic will be blocked, not just traffic from the 172.16.4.0/24 subnet.
- Only traffic from the 172.16.4.0/24 subnet is blocked, and all other traffic is allowed.
- An extended ACL must be used in this situation.

- 30 deny 172.23.16.0 0.0.15.255
- 15 deny 172.23.16.0 0.0.15.255
- 5 deny 172.23.16.0 0.0.15.255
- 5 deny 172.23.16.0 0.0.255.255

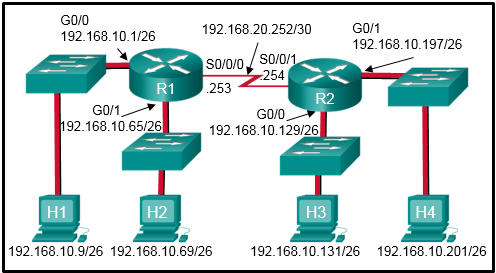
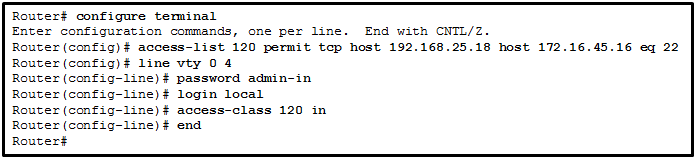
- An SSH connection is allowed from a workstation with IP 172.16.45.16 to a device with IP 192.168.25.18.
- An SSH connection is allowed from a workstation with IP 192.168.25.18 to a device with IP 172.16.45.16.
- A Telnet connection is allowed from a workstation with IP 192.168.25.18 to a device with IP 172.16.45.16.
- A Telnet connection is allowed from a workstation with IP 172.16.45.16 to a device with IP 192.168.25.18.

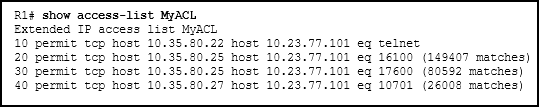
- The ACL is missing the deny ip any any ACE.
- The ACL is only monitoring traffic destined for 10.23.77.101 from three specific hosts.
- Because there are no matches for line 10, the ACL is not working.
- The router has not had any Telnet packets from 10.35.80.22 that are destined for 10.23.77.101.

- R2(config)# interface fastethernet 0/1
- R2(config-if)# ip access-group 101 out
- R2(config)# access-list 101 permit ip 192.168.1.0 255.255.255.0 192.168.2.0 255.255.255.0
- R2(config-if)# ip access-group 101 in
- R2(config)# access-list 101 permit ip any any
- R2(config)# interface fastethernet 0/0
- R2(config)# access-list 101 permit ip host 192.168.1.1 host 192.168.2.1
access-list 100 permit ip host 192.168.10.1 any
access-list 100 deny icmp 192.168.10.0 0.0.0.255 any echo
access-list 100 permit ip any any
Which two actions are taken if the access list is placed inbound on a router Gigabit Ethernet port that has the IP address 192.168.10.254 assigned? (Choose two.)
- Only Layer 3 connections are allowed to be made from the router to any other network device.
- Devices on the 192.168.10.0/24 network are not allowed to reply to any ping requests.
- Devices on the 192.168.10.0/24 network can sucessfully ping devices on the 192.168.11.0 network.
- A Telnet or SSH session is allowed from any device on the 192.168.10.0 into the router with this access list assigned.
- Only the network device assigned the IP address 192.168.10.1 is allowed to access the router.

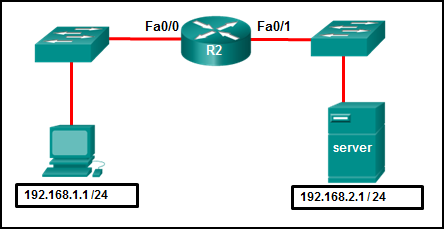
- The commands are added at the end of the existing Managers ACL.
- The commands overwrite the existing Managers ACL.
- The commands are added at the beginning of the existing Managers ACL.
- The network administrator receives an error that states that the ACL already exists.
- port scan attack
- SYN flood attack
- session hijacking attack
- reset attack
- DHCP
- DNS
- ICMP
- HTTP or HTTPS

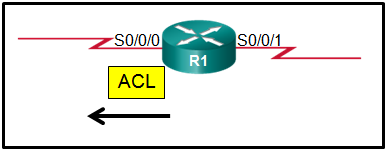
- The traffic is dropped.
- The source IP address is checked and, if a match is not found, traffic is routed out interface serial 0/0/1.
- The resulting action is determined by the destination IP address.
- The resulting action is determined by the destination IP address and port number.

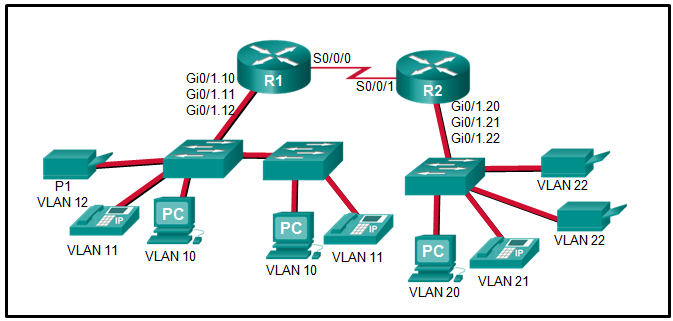
- inbound
- R2 S0/0/1
- R1 Gi0/1.12
- outbound
- R1 S0/0/0
- R2 Gi0/1.20
- They are configured in the interface configuration mode.
- They can be configured to filter traffic based on both source IP addresses and source ports.
- They can be created with a number but not with a name.
- They filter traffic based on source IP addresses only.
- Place identical restrictions on all vty lines.
- Remove the vty password since the ACL restricts access to trusted users.
- Apply the ip access-group command inbound.
- Use only extended access lists.

Refer to the exhibit. An administrator first configured an extended ACL as shown by the output of the show access-lists command. The administrator then edited this access-list by issuing the commands below.
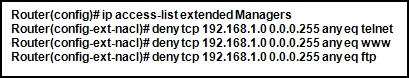
Router(config)# ip access-list extended 101 Router(config-ext-nacl)# no 20 Router(config-ext-nacl)# 5 permit tcp any any eq 22 Router(config-ext-nacl)# 20 deny udp any anyWhich two conclusions can be drawn from this new configuration? (Choose two.)
- TFTP packets will be permitted.
- Ping packets will be permitted.
- Telnet packets will be permitted.
- SSH packets will be permitted.
- All TCP and UDP packets will be denied.
- access-list 103 deny tcp host 192.168.10.0 any eq 23
access-list 103 permit tcp host 192.168.10.1 eq 80 - access-list 103 permit tcp 192.168.10.0 0.0.0.255 any eq 80
access-list 103 deny tcp 192.168.10.0 0.0.0.255 any eq 23 - access-list 103 permit 192.168.10.0 0.0.0.255 host 172.17.80.1
access-list 103 deny tcp 192.168.10.0 0.0.0.255 any eq telnet - access-list 103 permit tcp 192.168.10.0 0.0.0.255 host 172.17.80.1 eq 80
access-list 103 deny tcp 192.168.10.0 0.0.0.255 any eq 23
- mitigation
- exploit
- vulnerability
- threat

- extended ACL outbound on R2 WAN interface towards the internet
- standard ACL inbound on R1 vty lines
- extended ACLs inbound on R1 G0/0 and G0/1
- extended ACL outbound on R2 S0/0/1
- to add a text entry for documentation purposes
- to generate and send an informational message whenever the ACE is matched
- to identify any IP address
- to identify one specific IP address
- Internet architects planned for network security from the beginning.
- Early Internet users often engaged in activities that would harm other users.
- Internal threats can cause even greater damage than external threats.
- Threats have become less sophisticated while the technical knowledge needed by an attacker has grown.
- spam
- social engineering
- DDoS
- anonymous keylogging
- They target specific individuals to gain corporate or personal information.
- They probe a group of machines for open ports to learn which services are running.
- They are maliciously formed code segments used to replace legitimate applications.
- They are infected machines that carry out a DDoS attack.
- man-in-the-middle attack
- SYN flood attack
- DoS attack
- ICMP attack
- host
- most
- gt
- some
- any
- all
- Inbound ACLs are processed before the packets are routed while outbound ACLs are processed after the routing is completed.
- In contrast to outbound ALCs, inbound ACLs can be used to filter packets with multiple criteria.
- On a network interface, more than one inbound ACL can be configured but only one outbound ACL can be configured.
- Inbound ACLs can be used in both routers and switches but outbound ACLs can be used only on routers.
- All TCP traffic is permitted, and all other traffic is denied.
- Traffic originating from 172.16.4.0/24 is permitted to all TCP port 80 destinations.
- All traffic from 172.16.4.0/24 is permitted anywhere on any port.
- The command is rejected by the router because it is incomplete.
- access-list 101 permit tcp any host 192.168.1.1 eq 80
- access-list 101 permit tcp host 192.168.1.1 eq 80 any
- access-list 101 permit tcp host 192.168.1.1 any eq 80
- access-list 101 permit tcp any eq 80 host 192.168.1.1

CCNA 3 v7 Modules 3 – 5: Network Security Exam Answers 46
- Inbound ACLs must be routed before they are processed.
- The ACL is implicitly denying access to all the servers.
- Named ACLs require the use of port numbers.
- The ACL is applied to the interface using the wrong direction.
- to secure administrative access to the router
- to remove an ACL from an interface
- to remove a configured ACL
- to apply a standard ACL to an interface
- symmetric encryption algorithm
- data integrity
- exploit
- risk

CCNA 3 v7 Modules 3 – 5: Network Security Exam Answers 49
- standard ACL inbound on R2 WAN interface connecting to the internet
- standard ACL outbound on R2 WAN interface towards the internet
- standard ACL inbound on R1 G0/0
- standard ACL outbound on R1 G0/0

CCNA 3 v7 Modules 3 – 5: Network Security Exam Answers 42
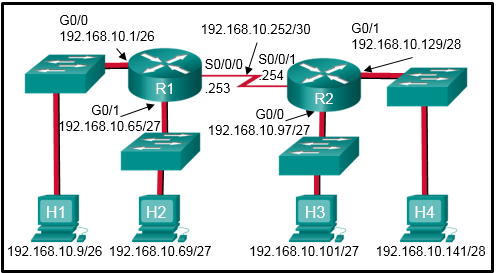
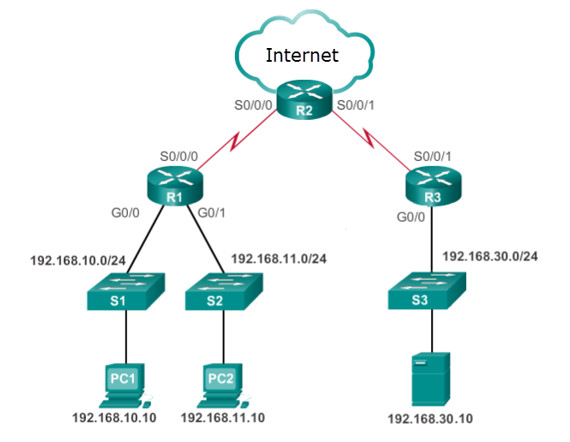
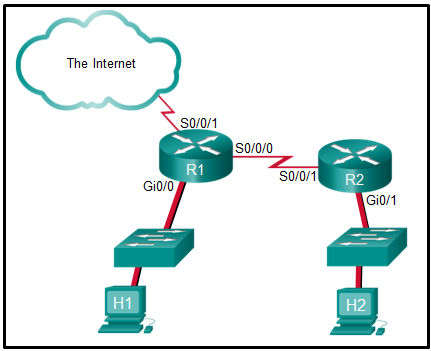
- Apply an inbound standard ACL on R1 Gi0/0.
- Apply an inbound extended ACL on R2 Gi0/1.
- Apply an outbound extended ACL on R1 S0/0/1.
- Apply an inbound extended ACL on R1 Gi0/0.
- Apply an outbound standard ACL on R2 S0/0/1.
- to apply an extended ACL to an interface
- to secure management traffic into the router
- to secure administrative access to the router
- to display all restricted traffic
- DNS amplification and reflection
- ARP cache poisoning
- DNS cache poisoning
- domain generation
- It can stop malicious packets.
- It is deployed in offline mode.
- It has no impact on latency.
- It is primarily focused on identifying possible incidents.
- vulnerability
- threat
- asset
- exploit
- standard ACL inbound on R1 vty lines
- extended ACLs inbound on R1 G0/0 and G0/1
- extended ACL inbound on R3 G0/0
- extended ACL inbound on R3 S0/0/1
- adware
- DDoS
- phishing
- social engineering
- spyware
- launching a security countermeasure to mitigate a Trojan horse
- downloading and installing too many software updates at one time
- attempting to write more data to a memory location than that location can hold
- sending too much information to two or more interfaces of the same device, thereby causing dropped packets
- sending repeated connections such as Telnet to a particular device, thus denying other data sources
- authentication
- availability
- confidentiality
- integrity












0 commentaires:
Enregistrer un commentaire