1. Which troubleshooting tool would a network administrator
use to check the Layer 2 header of frames that are leaving a particular
host?
R1# copy running-config tftp
Address or name of remote host [ ]?
When the router prompts for an address or remote host name, what IP address should the administrator enter at the prompt?
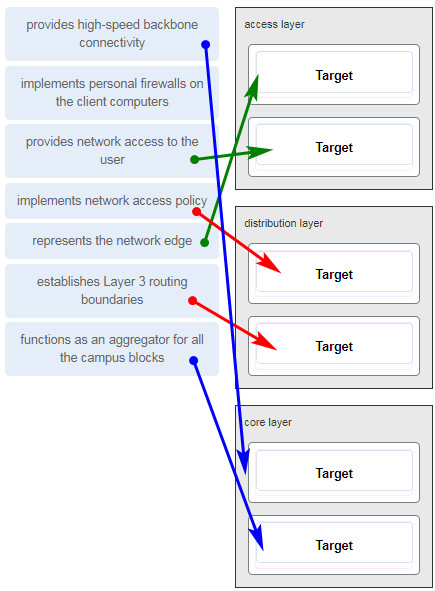
38. Match the borderless switched network guideline description to the principle. (Not all options are used.)
39. What are two characteristics of the best-effort QoS model? (Choose two.)
- knowledge base
- protocol analyzer
- CiscoView
- baselining tool

- They have different routing processes.
- They have different router IDs.
- They are in different subnets.
- The connecting interfaces are configured as passive.
- data
- video
- voice
- show file systems
- dir
- lldp enable
- service timestamps log datetime
- buffering
- latency
- queuing
- jitter
- A trust boundary identifies the location where traffic cannot be remarked.
- A trust boundary only allows traffic to enter if it has previously been marked.
- A trust boundary identifies which devices trust the marking on packets that enter a network.
- A trust boundary only allows traffic from trusted endpoints to enter the network.
- Decrease buffer space.
- Disable queuing mechanisms.
- Drop lower-priority packets.
- Prevent bursts of traffic.
- Increase link capacity.
- SNMPv2 for in-band management with read-write community strings
- SNMPv1 with out-of-band management in a private subnet
- SNMPv3 configured with the auth security level
- SNMP community strings
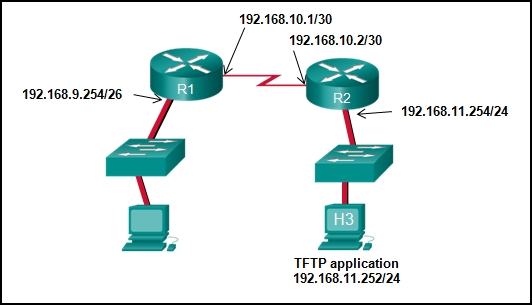
R1# copy running-config tftp
Address or name of remote host [ ]?
When the router prompts for an address or remote host name, what IP address should the administrator enter at the prompt?

- 192.168.9.254
- 192.168.10.2
- 192.168.11.252
- 192.168.11.254
- 192.168.10.1
- determines which server to send system log files to
- synchronizes the system clock with the time source with IP address 10.1.1.1
- identifies the server on which to store backup configurations
- ensures that all logging will have a time stamp associated with it
- providing redundant links that dynamically block or forward traffic
- grouping two devices to share a virtual IP address
- grouping multiple physical ports to increase bandwidth between two switches
- providing redundant devices to allow traffic to flow in the event of device failure
- access and core layers collapsed into one tier, and the distribution layer on a separate tier
- distribution and core layers collapsed into one tier, and the access layer on a separate tier
- access, distribution, and core layers collapsed into one tier, with a separate backbone layer
- access and distribution layers collapsed into one tier, and the core layer on a separate tier
- to select a routing protocol
- to determine what kind of equipment to implement
- to design a network according to a proper model
- to identify future abnormal network behavior
- to evaluate security vulnerabilities in the network
- to determine if the network can deliver the required policies
- The computer has an incorrect subnet mask.
- The computer has an invalid default gateway address.
- The cable is not connected properly to the NIC.
- The computer has an invalid IP address.
- Gather information.
- Narrow the scope.
- Document the symptoms.
- Determine ownership.
- Determine the symptoms.
- LLQ
- CBWFQ
- WFQ
- FIFO
- Voice traffic latency should not exceed 150 ms.
- Voice traffic is unpredictable and inconsistent.
- Voice traffic requires at least 384 kbs of bandwidth.
- Voice traffic consumes lots of network resources.
- Dropped voice packets are not retransmitted.
- TCP
- ICMP
- IP
- UDP
- delay
- packet addressing
- jitter
- packet routing
- link speed
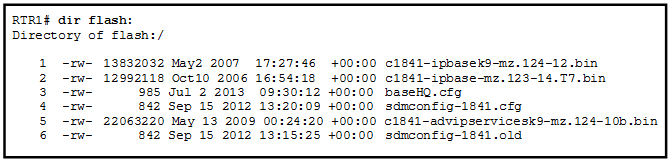
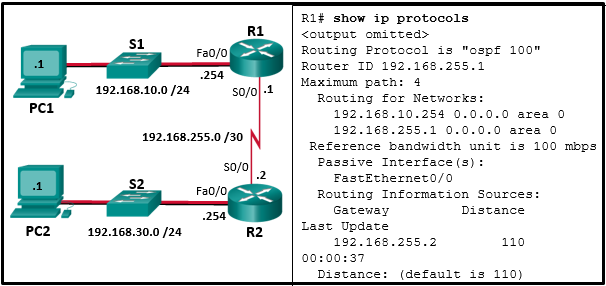
- name of the configuration file that is currently stored on the router
- configuration register value
- name of the configuration file that is stored on the TFTP server
- router IP address
- TFTP server IP address

- The router selects an image depending on the boot system command in the configuration.
- The router selects an image depending on the value of the configuration register.
- The router selects the third Cisco IOS image because it is the most recent IOS image.
- The router selects the third Cisco IOS image because it contains the advipservicesk9 image.
- The router selects the second Cisco IOS image because it is the smallest IOS image.

- switch
- hub
- router
- repeater
- Source Route Bridge
- to select the type of logging information that is captured
- to periodically poll agents for data
- to provide statistics on packets that are flowing through a Cisco device
- to provide traffic analysis
- to gather logging information for monitoring and troubleshooting
- to specify the destinations of captured messages
- to collect data from SNMP agents
- to send and retrieve network management information
- to change configurations on SNMP agents
- to store data about a device
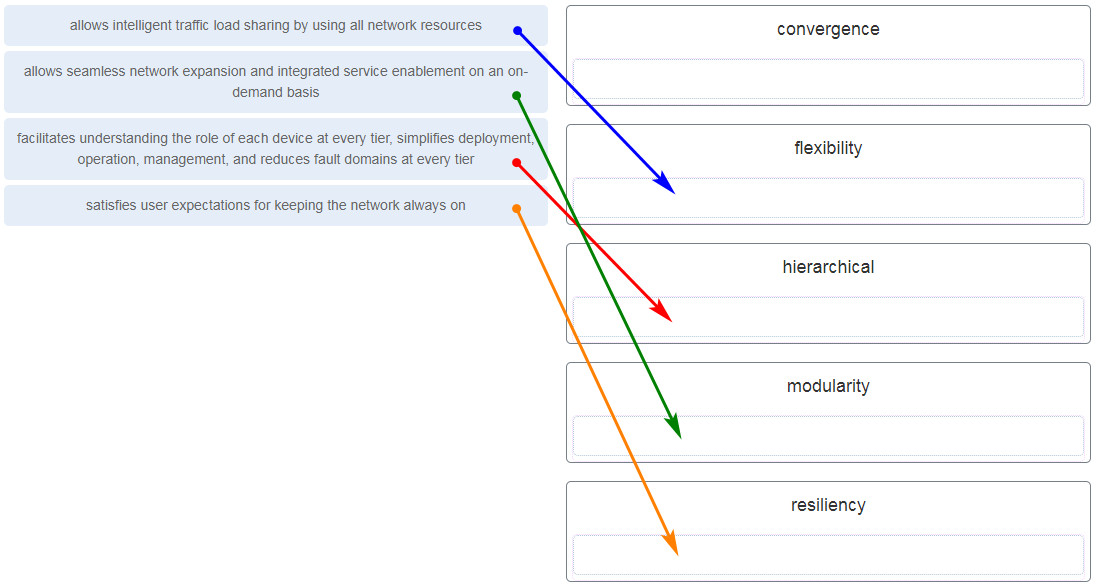
- the reduction in the number of redundant devices and connections in the network core
- the installation of only enterprise class equipment throughout the network
- the deployment of distribution layer switches in pairs and the division of access layer switch connections between them
- the configuration of all access layer devices to share a single gateway
- add alternate physical paths for data to traverse the network
- continually purchase backup equipment for the network
- implement STP portfast between the switches on the network
- immediately replace a non-functioning module, service or device on a network
- increased flexibility
- increased network management options
- decreased number of critical points of failure
- reduced costs
- increased bandwidth availability
- aggregates Layer 2 broadcast domains
- provides access to the user
- aggregates Layer 3 routing boundaries
- provides fault isolation
- ability to have multiple forwarding paths through the switched network based on VLAN number(s)
- ability to build a routing table
- ability to provide power to directly-attached devices and the switch itself
- ability to aggregate multiple ports for maximum data throughput

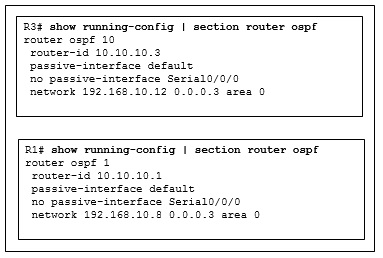
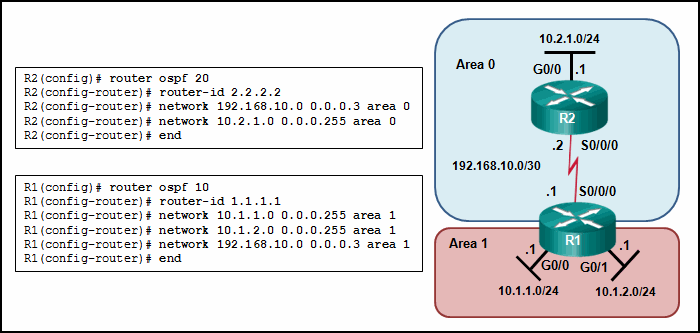
- The serial interfaces are not in the same area.
- The process numbers are not the same in both routers.
- A backbone router cannot establish an adjacency with an ABR router.
- The router ID values are not the same in both routers.
- whenever high network use is detected, so that how the network performs under stress can be monitored
- during quiet vacation periods, so that the level of non-data traffic can be determined
- at the same time each day across a set period of average working days, so that typical traffic patterns can be established
- at random times during a 10 week period, so that abnormal traffic levels can be detected

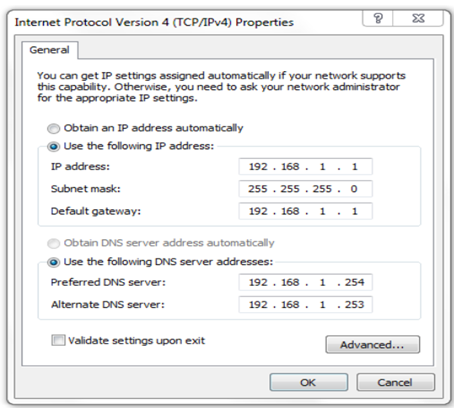
- The preferred DNS address is incorrect.
- The default gateway address is incorrect.
- The settings were not validated upon exit.
- There should not be an alternate DNS server.

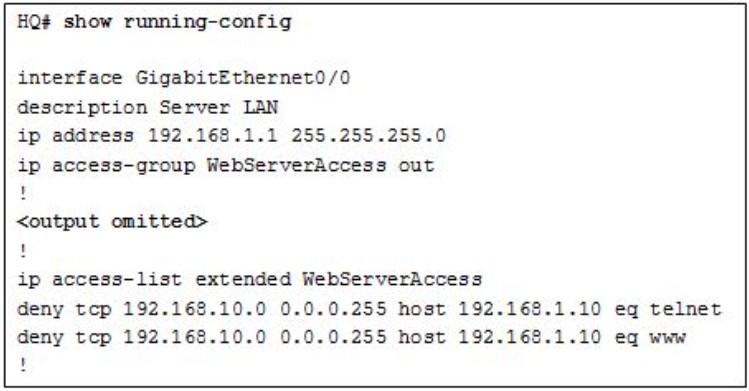
- Inbound ACLs must be routed before they are processed.
- The ACL is implicitly denying access to all the servers.
- Named ACLs require the use of port numbers.
- The ACL is applied to the interface using the wrong direction.

- Disconnect the serial link between router R1 and R2.
- Turn off OSPFv2.
- Implement the network 192.168.255.0 0.0.0.3 area 0 command on router R1.
- Test Layer 3 connectivity between the directly connected routers.
- voice
- video
- data
- show cdp interface
- ntp server 10.10.14.9
- service timestamps log datetime
- clock timezone PST -7

38. Match the borderless switched network guideline description to the principle. (Not all options are used.)

39. What are two characteristics of the best-effort QoS model? (Choose two.)
- It allows end hosts to signal their QoS needs to the network.
- It uses a connection-oriented approach with QoS.
- It provides preferential treatment for voice packets.
- It does not provide a delivery guarantee for packets.
- It treats all network packets in the same way.
- Data communications are sensitive to jitter.
- Legacy equipment is unable to transmit voice and video without QoS.
Correct Response - Voice and video communications are more sensitive to latency.
- Data communications must be given the first priority.
R1(config)# boot system tftp://c1900-universalk9-mz.SPA.152-4.M3.bin R1(config)# boot system romWhat is the effect of the command sequence?
- On next reboot, the router will load the IOS image from ROM.
- The router will search and load a valid IOS image in the sequence of flash, TFTP, and ROM.
- The router will copy the IOS image from the TFTP server and then reboot the system.
- The router will load IOS from the TFTP server. If the image fails to load, it will load the IOS image from ROM.
- An SNMP agent that resides on a managed device collects information about the device and stores that information remotely in the MIB that is located on the NMS.
- A set request is used by the NMS to change configuration variables in the agent device.
- An NMS periodically polls the SNMP agents that are residing on managed devices by using traps to query the devices for data.
- A get request is used by the SNMP agent to query the device for data.

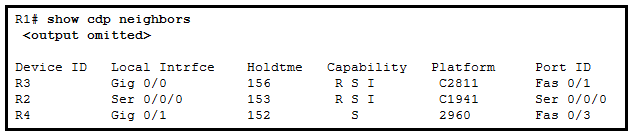
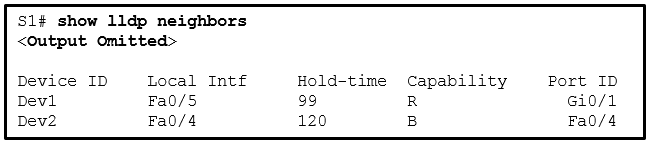
- Dev1 is connected to interface Fa0/5 of S1.
- Dev1 is a switch with mixed types of interfaces.
- Dev2 is a switch.
- Dev1 is connected to interface Fa0/4 of Dev2.
- S1 has only two interfaces.
- distribution
- network access
- data link
- enterprise
- access
- core

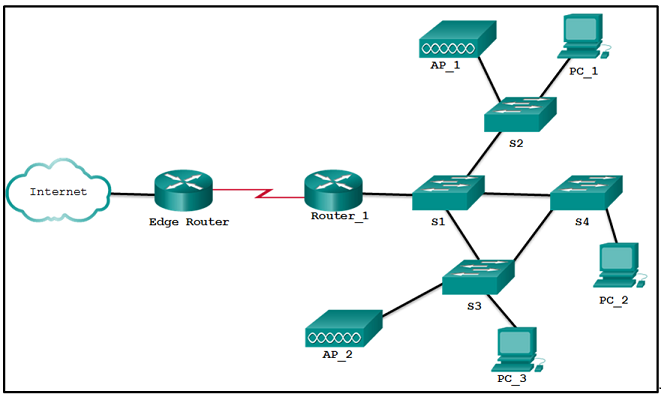
- S4 and PC_2
- PC_3 and PC_2
- PC_3 and AP_2
- S1 and S4
- AP_2 and AP_1
- This is network application software that prevents the failure of a single network device.
- The failure of a switch block will not impact all end users.
- This is a security feature that is available on all new Catalyst switches.
- A single core router provides all the routing between VLANs.












0 commentaires:
Enregistrer un commentaire